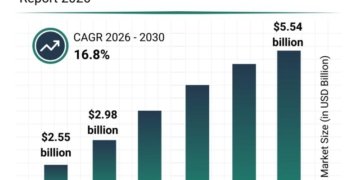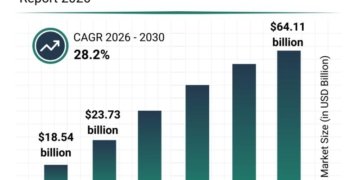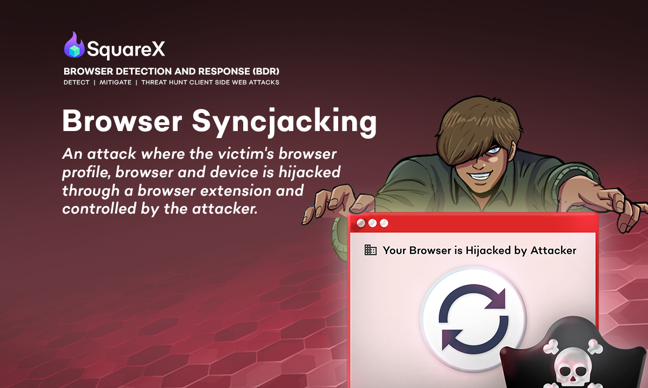
SquareX discloses a new attack technique that shows how malicious extensions can be used to completely hijack the browser, and eventually, the whole device.
PALO ALTO, Calif., Jan. 30, 2025 (GLOBE NEWSWIRE) — Browser extensions have been under the spotlight in enterprise security news recently due to the wave of OAuth attacks on Chrome extension developers and data exfiltration attacks. However, until now, due to the limitations browser vendors place on the extension subsystem and extensions, it was thought to be impossible for extensions to gain full control of the browser, much less the device.
SquareX researchers Dakshitaa Babu, Arpit Gupta, Sunkugari Tejeswara Reddy and Pankaj Sharma debunked this belief by demonstrating how attackers can use malicious extensions to escalate privileges to conduct a full browser and device takeover, all with minimal user interaction. Critically, the malicious extension only requires read/write capabilities present in the majority of browser extensions on the Chrome Store, including common productivity tools like Grammarly, Calendly, and Loom, desensitizing users from granting these permissions. This revelation suggests that virtually any browser extension could potentially serve as an attack vector if created or taken over by an attacker. To the best of our understanding, extensions submitted to the Chrome Store requesting these capabilities are not put through additional security scrutiny at the time of this writing.
The browser syncjacking attack can be broken up into three parts: how the extension silently adds a profile managed by the attacker, hijacks the browser and eventually gains full control of the device.
Profile Hijacking
The attack begins with an employee installing any browser extension – this could involve publishing one that masquerades as an AI tool or taking over existing popular extensions that may have up to millions of installations in aggregate. The extension then “silently” authenticates the victim into a Chrome profile managed by the attacker’s Google Workspace. This is all done in an automated manner in a background window, making the whole process almost imperceptible to the victim. Once this authentication occurs, the attacker has full control over the newly managed profile in the victim’s browser, allowing them to push automated policies such as disabling safe browsing and other security features.
Using a very clever social engineering attack that exploits trusted domains, the adversary can then further escalate the profile hijacking attack to steal passwords from the victim’s browser. For example, the malicious extension can open and modify Google’s official support page on how to sync user accounts to prompt the victim to perform the sync with just a few clicks. Once the profile is synced, attackers have full access to all credentials and browsing history stored locally. As this attack only leverages legitimate sites and has no visible sign that it has been modified by the extension, it will not trigger any alarm bells in any security solutions monitoring the network traffic.
Browser Takeover
To achieve a full browser takeover, the attacker essentially needs to convert the victim’s Chrome browser into a managed browser. The same extension monitors and intercepts a legitimate download, such as a Zoom update, and replaces it with the attacker’s executable, which contains an enrollment token and registry entry to turn the victim’s Chrome browser into a managed browser. Thinking that they downloaded a Zoom updater, the victim executes the file, which ends up installing a registry entry that instructs the browser to become managed by the attacker’s Google Workspace. This allows the attacker to gain full control over the victim’s browser to disable security features, install additional malicious extensions, exfiltrate data and even silently redirect users to phishing sites. This attack is extremely potent as there is no visual difference between a managed and unmanaged browser. For a regular user, there is no telltale sign that a privilege escalation has occurred unless the victim is highly security aware and goes out of their way to regularly inspect their browser settings and look for associations with an unfamiliar Google Workspace account.
Device Hijacking
With the same downloaded file above, the attacker can additionally insert registry entries required for the malicious extension to message native apps. This allows the extension to directly interact with local apps without further authentication. Once the connection is established, attackers can use the extension in conjunction with the local shell and other available native applications to secretly turn on the device camera, capture audio, record screens and install malicious software – essentially providing full access to all applications and confidential data on the device.
The browser syncjacking attack exposes a fundamental flaw in the way remote-managed profiles and browsers are managed. Today, anyone can create a managed workspace account tied to a new domain and a browser extension without any form of identity verification, making it impossible to attribute these attacks. Unfortunately, most enterprises currently have zero visibility into the browser – most do not have managed browsers or profiles, nor any visibility to the extensions employees are installing often based on trending tools and social media recommendations.
What makes this attack particularly dangerous is that it operates with minimal permissions and nearly no user interaction, requiring only a subtle social engineering step using trusted websites – making it almost impossible for employees to detect. While recent incidents like the Cyberhaven breach have already compromised hundreds, if not thousands of organizations, those attacks required relatively complex social engineering to operate. The devastatingly subtle nature of this attack – with an extremely low threshold of user interaction – not only makes this attack extremely potent, but also sheds light on the terrifying possibility that adversaries are already using this technique to compromise enterprises today.
Unless an organization chooses to completely block browser extensions via managed browsers, the browser syncjacking attack will completely bypass existing blacklists and permissions-based policies. SquareX’s founder, Vivek Ramachandran, says, “This research exposes a critical blind spot in enterprise security. Traditional security tools simply can’t see or stop these sophisticated browser-based attacks. What makes this discovery particularly alarming is how it weaponizes seemingly innocent browser extensions into complete device takeover tools, all while flying under the radar of conventional security measures like EDRs and SASE/SSE Secure Web Gateways. A Browser Detection-Response solution isn’t just an option anymore – it’s a necessity. Without visibility and control at the browser level, organizations are essentially leaving their front door wide open to attackers. This attack technique demonstrates why security needs to ‘shift up’ to where the threats are actually happening: in the browser itself.”
SquareX has been conducting pioneering security research on browser extensions, including the DEF CON 32 talk Sneaky Extensions: The MV3 Escape Artists that revealed multiple MV3 compliant malicious extensions. This research team was also the first to discover and disclose the OAuth attack on Chrome extension developers one week before the Cyberhaven breach. SquareX was also responsible for the discovery of Last Mile Reassembly attacks, a new class of client-side attacks that exploits architectural flaws and completely bypasses all Secure Web Gateway solutions. Based on this research, SquareX’s industry-first Browser Detection and Response solution protects enterprises against advanced extension-based attacks including device hijacking attempts by conducting dynamic analysis on all browser extension activity at runtime, providing a risk score to all active extensions across the enterprise and further identifying any attacks that they may be vulnerable to.
For more information about the browser syncjacking attack, additional findings from this research are available at sqrx.com/research.
About SquareX
SquareX helps organizations detect, mitigate and threat-hunt client-side web attacks happening against their users in real time.
SquareX’s industry-first Browser Detection and Response (BDR) solution, takes an attack-focused approach to browser security, ensuring enterprise users are protected against advanced threats like malicious QR Codes, Browser-in-the-Browser phishing, macro-based malware and other web attacks encompassing malicious files, websites, scripts, and compromised networks.
Additionally, with SquareX, enterprises can provide contractors and remote workers with secure access to internal applications, enterprise SaaS, and convert the browsers on BYOD / unmanaged devices into trusted browsing sessions.
Contact
Head of PR
Junice Liew
SquareX
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/d184d7d1-727f-4b63-8629-932464610908